A couple of year ago – I wrote a post about handling SSL Junctions being marked as unavailable. The fix I did then was to disable Client Cert Auth on the back-end. Since then – I’ve come across a couple more issues and have some better solutions and more understanding of the issue.
For the issue I had last time – the back-end was *optionally* asking for a Client Certificate. The WebSEAL process is indiscriminate with how it supplies a certificate – so it will send it’s private key even if it’s not accepted by the back end. There’s a simple fix for this. WebSEAL has a configuration item to specify a junction key file- seperate from the one that hosts the private key for the instance. And if you create a keystore that does not contain a private key – then one wont be sent to any junctioned servers.
To set this up – create a keystore called “blank”. Load in all the signer certs required but leave the private cert blank. Setup the following in the [junction] stanza – noting that it is for the entire instance – cannot be junction specific.
jct-cert-keyfile = blank.kdb jct-cert-keyfile-stash = blank.sth
You can also set this up in the GUI. It’s the “Junction Keystore” setting on the SSL Tab.
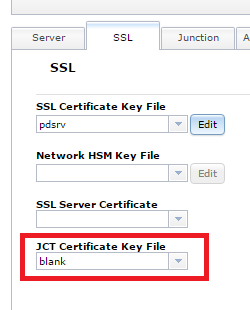
I recently ran into a more complex issue. Even with that blank keystore in place – I still couldn’t get the junction to connect. I constantly got the error:
webseald WARNING wiv ssl SSLConnection.cpp 2049 0x7fc532411700 DPWIV1210W Function call, gsk_secure_soc_init, failed error: 0000019e GSK_ERROR_BAD_CERT.
Various searches led basically no-where. I found a technote that talked about jct-nist-compliance but that didn’t seem to help. In the end – I tried the disable-tls-v1 and disable-tls-v11 settings. For some reason – ISAM and this particular back-end could not negotiate a TLS connection. And therefore the Ping process failed. And therefore the junction was always offline. When I forced ISAM to only use TLS 1.2 for the junction:
[junction:/myjunction] disable-tls-v1 = yes disable-tls-v11 = yes disable-tls-v12 = no
then the junction became healthy at last.